Categories
Feb 26, 2026
4 min Read
Running scans using different SAST, DAST, IaaC, and proprietary scanners is only half of t...
vulnerability managementASPMintegrations
Feb 23, 2026
4 min Read
The "Fix everything High/Critical in 30 days" policy is a standard in the industry, but in...
Feb 21, 2026
4 min Read
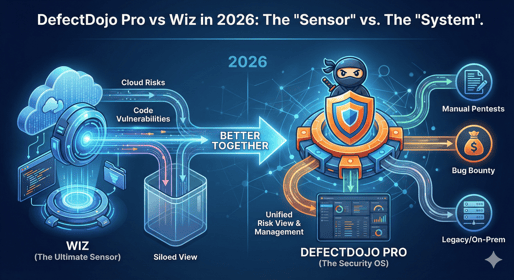
In 2026, Wiz is the "Google" of cloud security: fast, ubiquitous, and incredibly good at f...
Feb 20, 2026
5 min Read
Building a top-tier open-source vulnerability management stack requires distinguishing bet...
Feb 20, 2026
3 min Read
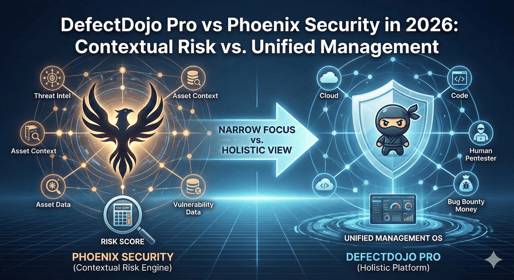
In 2026, "Risk-Based Vulnerability Management" (RBVM) is the industry standard. Both Defec...
Feb 20, 2026
4 min Read
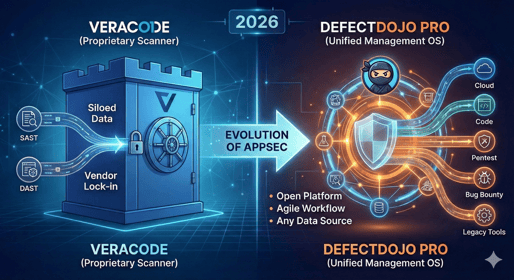
In 2026, Veracode has successfully integrated Longbow Security to create "Veracode Risk Ma...