Risk-Based Vulnerability Management
For Risk-Based Vulnerability Management
DefectDojo is the command center of your security program, centralizing the results from all your security tools to create a unified approach to vulnerability management. DefectDojo enriches all CVEs with real-world exploitability data from KEV, EPSS, and other sources to create a true risk-based view of your findings, vulnerabilities, and exposures.


Risk Prioritization

Unified Security

Increase Efficiency
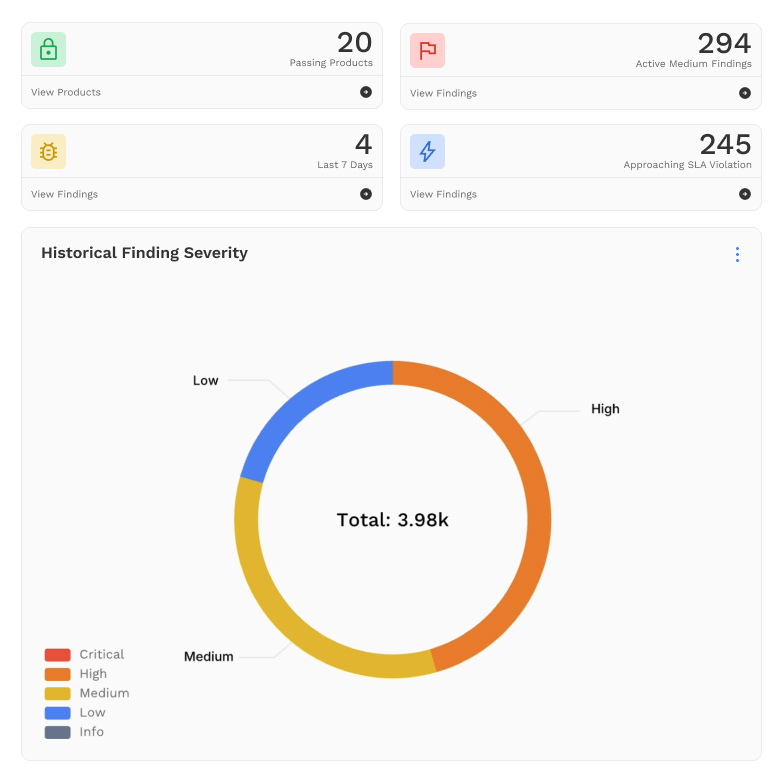
Security Findings Consolidation
Ingests and aggregates findings from a wide array of security tools into one centralized platform.
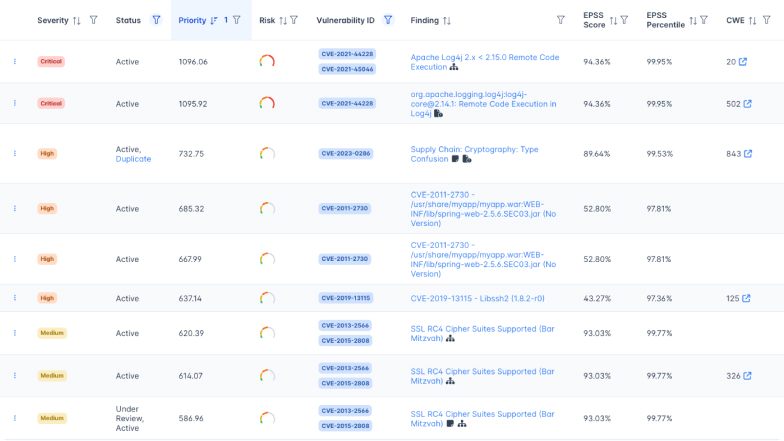
Automatic Data Enrichment
Automatically enhances CVE data with actionable intelligence from external sources to provide deeper context.
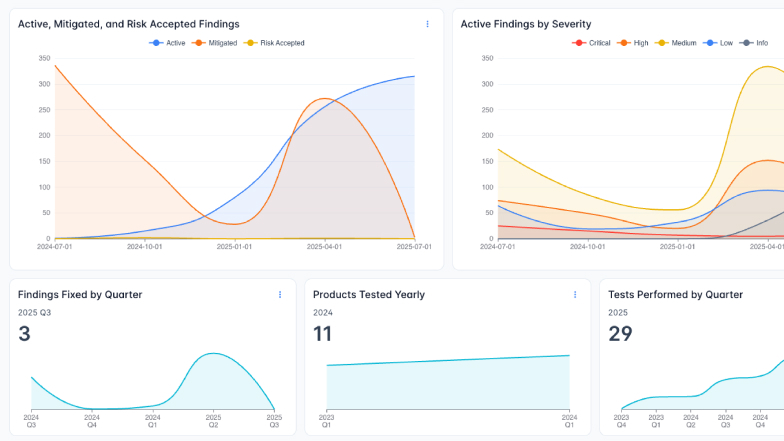
Threat Intelligence Integration
Integrates directly with critical threat intelligence feeds, including the CISA Known Exploited Vulnerabilities (KEV) catalog and the Exploit Prediction Scoring System (EPSS).
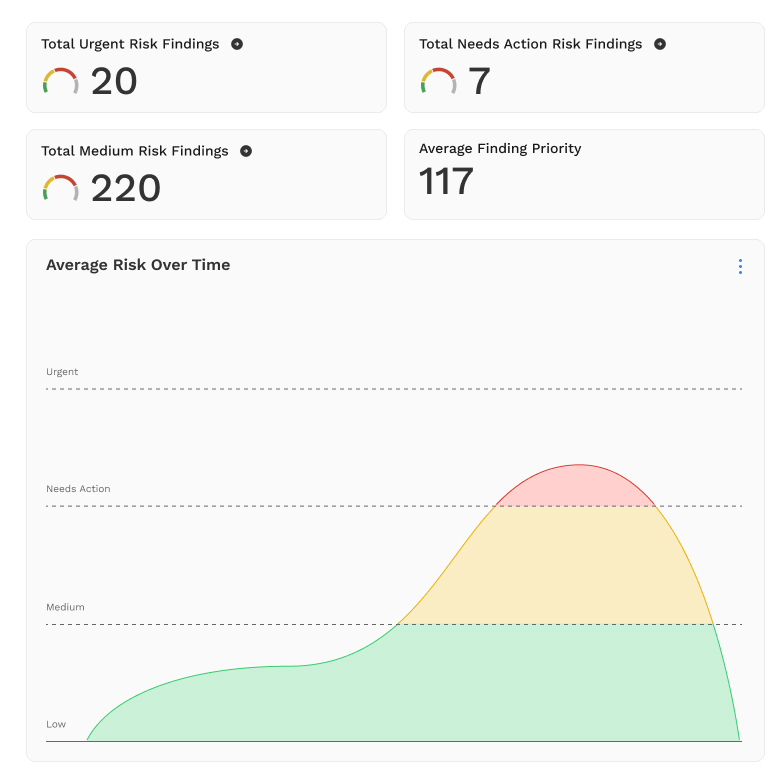
Centralized Vulnerability Database
Creates a single source of truth for all findings, vulnerabilities, and exposures across the organization.

Testimonials
Start Your Free Trial Today
Unify your security pipeline and orchestrate peace of mind with DefectDojo. We are security experts and here to help.