Feb 16, 2026
4 min Read
In 2026, the challenge isn't finding vulnerability scanners—it's surviving the output. Wit...
Feb 16, 2026
3 min Read
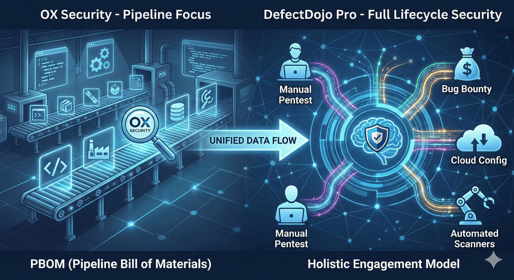
In 2026, software supply chain security is table stakes. While OX Security made waves with...
Feb 15, 2026
4 min Read
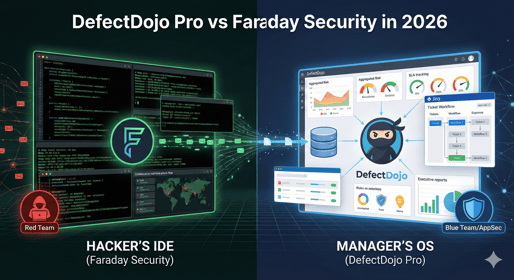
In 2026, many organizations confuse Faraday and DefectDojo Pro because both are deeply roo...
Feb 15, 2026
4 min Read
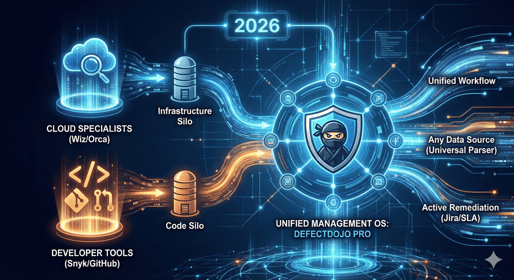
In 2026, asking "What is the best ASPM tool?" is a bit like asking "What is the best tool ...
Feb 15, 2026
4 min Read
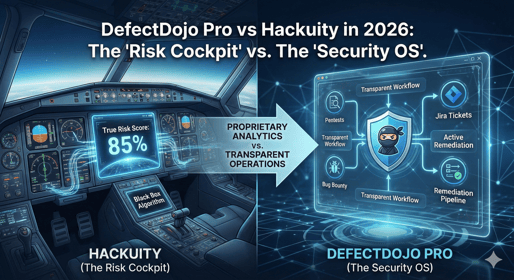
In 2026, Hackuity has carved out a niche as the "Vulnerability Operations Center." Its pri...
Feb 14, 2026
3 min Read
In 2026, the CIO's mandate is consolidation. "Put it all in ServiceNow" is the common refr...