
First, if you’re not familiar with ASPM, ASPM is short for “Application Security Posture Management” - 🤦🏻, and everyone is talking about it because Gartner has stated that ASPM and API Security are the two most critical areas in modern security programs.
I have never seen a vendor-created term truly stick in security, but given the weight Gartner and others are putting behind ASPM, it may be here to stay. ASPM in practice is not new, and is practically equivalent to the community-driven term, “DevSecOps”. So whether people use “ASPM”, “ASOC”, “DevSecOps”, or whatever current marketing jargon is resonating, at the end of the day the goal is the same: achieve high-quality security automation that doesn’t produce low quality results.
ASPM does have one key difference from other similar industry buzzwords, which is a focus on risk prioritization based on real exploitability. First’s EPSS (Exploit Prediction Scoring System) seems to be the standout with regard to exploitability-based scoring, and at DefectDojo, we’ve incorporated EPSS scoring into our platform to provide enriched data on the exploitability of a given security vulnerability. We do also offer more traditional CVSS scoring, which does factor in attack-surface area. The key difference to consider between these scoring systems is EPSS factors in actual public data on what is being exploited. Some will see that as positive, however if data is limited for a given CVE, the more traditional CVSS scoring may be a better barometer for your organization. Another option is utilizing the two through the lenses they work the best. If a vulnerability has a high EPSS score, it should definitely be prioritized, but just because a vulnerability doesn’t have a high EPSS score doesn’t conversely mean that it shouldn’t be prioritized. Taking a hybrid approach of examining both EPSS and CVSS will likely yield the best results with regard to risk-based vulnerability management.
Moving from research and theory to implementation, how do you select the best ASPM for your org?
-
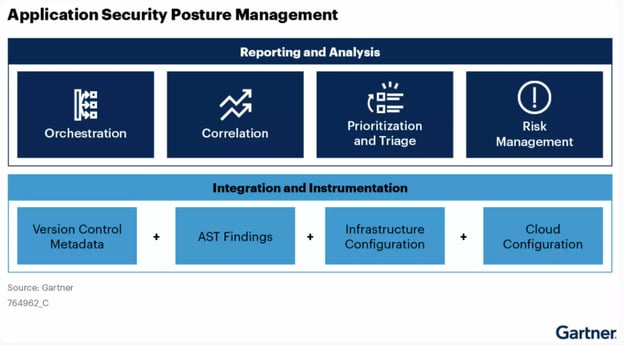
The key to an ASPM platform is aggregating and normalizing data from your security tools. Thus, it is important that your ASPM supports all of your security tools. If you can’t bring in all your tools, you can’t accurately track the posture of your organization.
-
ASPMs need to be flexible and offer multiple ways to absorb scans from your security tools. It is very likely that getting data into your ASPM cannot be a one size fits all approach as you’ll end up leaving data on the table which will greatly impact your ability to track, report, and remediate based on risk.
-
Your ASPM needs to be able to handle data at scale. Unfortunately the number of vulnerabilities in software is growing dramatically which means more data for your ASPM to chug through. It’s fairly easy to handle 10K findings from a perspective of scale, but will your solution hold up at 100K or 1M+ findings?
-
Your ASPM needs to be able to handle and document risk exceptions. Without a mechanism to manage risk exceptions, you’ll be stuck in a place where yet-another tool will be required for your security program to function. ASPMs should provide a single pane of glass for your appsec operations which risk exceptions are an important part of.
-
Your ASPM needs to do a good job of distilling and deduplicating findings from your various tools. Not all deduplication and distillation processes are equal. How well these functions work directly impacts how much mundane work your appsec team will still need to do (if any). Can your ASPM report on how findings change scan to scan? Can the deduplication functions work across multiple tools or just a single tool? Does the platform leverage machine learning or AI to get you better results week over week?
Both organizations and individuals can achieve business-changing wins through ASPM and security automation. What individuals can get out of this movement is a more reasonable work environment with tasks and KPIs that are actually possible. The job of being a security professional is an extremely difficult one, which contributes to the very short tenure from security engineers to CISOs. ASPMs can provide the relief security professionals deserve. Organizations can also scale security without having to invest in headcount at a linear ratio. Budgets are tight. ASPMs can provide both transformative efficiency and cost savings for organizations.