
DefectDojo is my life’s work. Ten years ago, Matt Tesauro and I set out to fix what we saw as fundamentally broken in AppSec & security at large – a lack of scalability driven by the need for security teams to grapple with security tools that were inaccurate, reported the same issue 100+ times, or lacked key details. If you can’t scale your security program to cover your entire company, you can’t accurately know what your greatest risks are and which risks you should prioritize. Scanners have come a long way, but the challenge of scaling and prioritizing persists. We asked ourselves, is it really possible to scale, centralize, consolidate, and deduplicate results from the entire landscape of security tools with minimal human involvement?
From security engineers to CISOs, security professionals have incredibly short tenures compared to their peers in other specialities. What we don’t want to admit is the job has been nearly impossible and security practitioners suffer from extreme burnout.We’ve changed that with DefectDojo. Now, it’s possible to get accurate and scalable security results that drive improved risk posture management.
At DefectDojo, we make end-to-end security testing without human intervention a reality by leveraging DevSecOps and machine learning. Automation is a key tenet of the DefectDojo ethos. If an action requires a human, you should only need to do it once. DefectDojo remembers the actions your security team takes, eliminating the need to constantly revise and adjust the results of your security scanners. At Rackspace, we used what would become DefectDojo to reduce our workload from 10 hour days to 2 hour days with 8 hours of foosball (Don’t tell my old boss. Sorry Jim if you see this).
DefectDojo was and is our secret weapon to be able to do our job, delivering the most accurate, prioritized findings across all our applications, while also achieving impressive ROI for our leadership. When Matt and I moved on from Rackspace to Pearson, we took Pearson from testing 44 applications a year to 414. That was an 840% increase in output, even though we lost half of our team due to downsizing. Pearson was so happy with these results that they sent Matt and myself on a PR tour to speak about our achievement and use it to attract and retain renowned security talent.
After Pearson, the wins continued to compound for the DefectDojo community at large. In late 2022, building on our open source heritage, we released the Pro Edition to insure the future of the platform for both OS and commercial users alike. Today, we’re grateful to work with security teams that are just starting their journey and some of the largest multinational corporations. DefectDojo is meant to be a force for good for all security practitioners and programs.
Not every team is ready to make the quantum leap to complete automation. We often see different levels of maturity within a single company. Wherever you are in the process, the platform is flexible to meet you where you are and help you mature your program to ultimately achieve your automation goals.
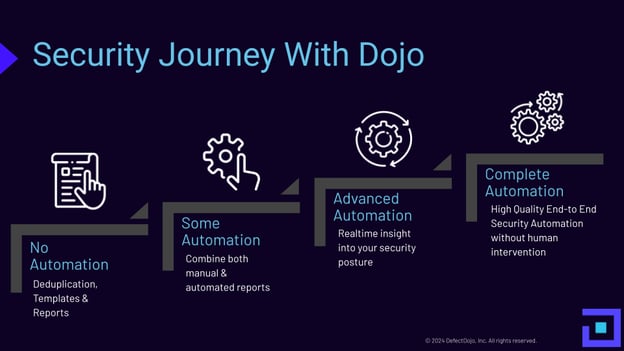
Where to start? First, DefectDojo serves as an aggregator for all of your security tools (currently 170+) to centralize results and create a distilled, consolidated, and accurate command center for your program. One tool to rule and wrangle them all so you don’t have to.
Once the data is aggregated, the next step is assessing which smart functions make sense for your usage to remove the work that humans would normally do.
.png?width=624&height=351&name=imageLikeEmbed%20(1).png)
.png?width=624&height=351&name=imageLikeEmbed%20(2).png)
We’ve seen DefectDojo reduce the work security engineers have to do by over 60%. Better yet, it’s the 60% they don’t like doing (consolidation, reporting, metrics), which means your security team can actually spend time on the work they enjoy and what you hired them to do, testing products and infrastructure.
Finally we ship those distilled results to where developers actually work (JIRA, etc.) Our data says that when findings land in developer backlogs they’re interacted with 12X more compared to traditional security reporting (throwing a PDF over the fence).
Once implemented, there is only one thing left to do. Take a breath and relax.